Security and Integrity
What is Research Security?
UTA's Research Security Program is established pursuant to National Security Presidential Memorandum-33, Texas Education Code Section 51.956 and outlined in UTA Policy. The Research Security Program is responsible for promoting secure research and protecting principal investigators (PIs) by mitigating the risk of foreign influence and intellectual property theft. This is accomplished through:
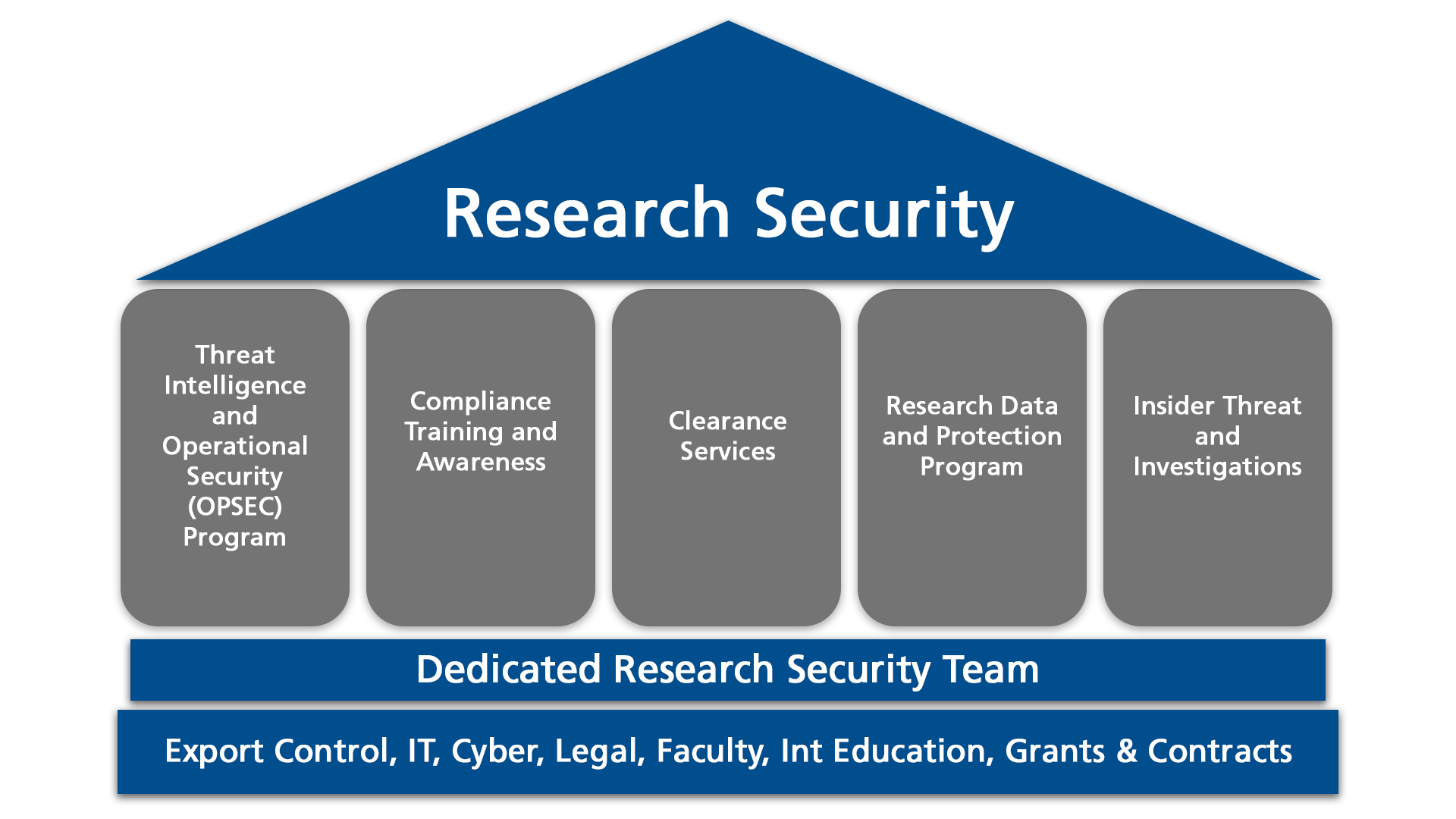
Threat Intelligence & Operational Security (OPSEC) Program
The threat intelligence team utilizes a variety of open-source intelligence (OSINT) and tools for preventing undue foreign influence on research.
Whenever conducting any of the following engagements, please reach out to [email protected] for due diligence:
Foreign Partnerships/Collaborations
Foreign Scholars (DS2019)
Foreign Supply Chain Vendors
Gifts received from a foreign country
Foreign Visitors
The OPSEC program works with faculty to create a custom research security risk mitigation plan for their lab space. Research Security will work directly with faculty to implement best security practices for their lab space. Please reach out to [email protected] to schedule an assessment.
Security Training, Awareness & Foreign Travel Reporting
Research Security offers online compliance training for the following mandatory trainings:
1. CUI Compliance Training
This training is mandatory for participation in a CUI project. It must be completed on a yearly basis.
2. Research Security Compliance Training
This training is mandatory for individual listed on a federal grant application. This training must be completed before submitting the grant application.
3. Foreign Travel Reporting:
Texas Executive Order GA-48 prohibits business travel to a Foreign Country of Concern (FCOC). Additional training and policy guidance is provided here.
Insider Threat and Investigations
What is an Insider?
An insider is any person who has or had authorized access to or knowledge of an organization’s resources, including personnel, facilities, information, equipment, networks, and systems.
What is an Insider Threat Program?
An insider threat program is designed to identify, prevent, and mitigate risks posed by individuals within an institution who may intentionally or unintentionally cause harm. institution. It focuses on monitoring activities, securing sensitive information, and ensuring compliance with security policies.
Three types of insider threats
- Negligence
- An insider of this type exposes an organization to a threat through carelessness. Negligent insiders are generally familiar with security and/or IT policies but choose to ignore them, creating risk for the organization. Examples include allowing someone to “piggyback” through a secure entrance point, misplacing or losing a portable storage device containing sensitive information and ignoring messages to install new updates and security patches.
- Accidental
An insider of this type mistakenly causes an unintended risk to an organization. Examples include mistyping an email address and accidentally sending a sensitive business document to a competitor, unknowingly or inadvertently clicking on a hyperlink, opening an attachment in a phishing email that contains a virus, or improperly disposing of sensitive documents.
- Malicious
- These individuals intentionally cause harm to the organization. They may steal sensitive information, sabotage systems, or engage in fraud for personal gain or to benefit a competitor.
Red Flags
Please be aware of “red flags” that you may notice.
- Unusual Access Patterns: Accessing sensitive information that is not relevant to their job duties.
- Policy Violations: Frequently breaking company policies or security protocols.
- Behavioral Changes: Sudden changes in behavior, attitude, or work performance.
- Excessive Downloading: Downloading or transferring large amounts of data without a clear business need.
- Bypassing Security: Attempting to bypass or disable security measures.
- Unauthorized Devices: Using unauthorized devices like USB drives or personal laptops.
- Disgruntlement: Expressing dissatisfaction or resentment towards the institution.
- Unusual Working Hours: Working odd hours without a valid reason.
If you See something, say something. Please reach out to [email protected] with any concerns you may have.